Problem with layer 7 attack
Hello my dear friends of this beloved forum.
As everyone knows, most schools, if not all schools are closed and with that all the kids are on the loose (burn the witch)!
I work with sales of minecraft hosting and recently I am having problems with DDoS Layer 7 attacks that make my php-fpm just overflow CPU usage.
I use nginx + php fpm.
I need urgent help to remedy this problem. I will be grateful for those who help me.
Here is a screenshot of the attack:
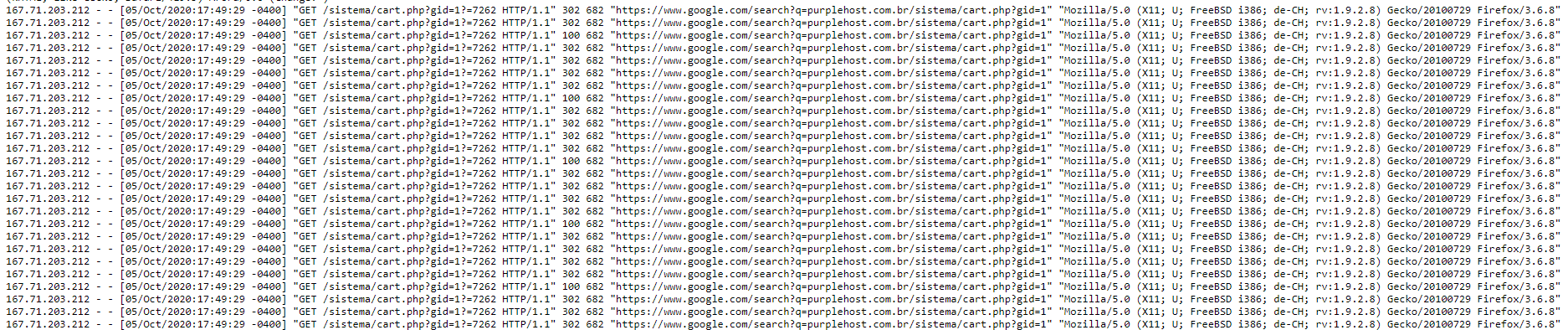
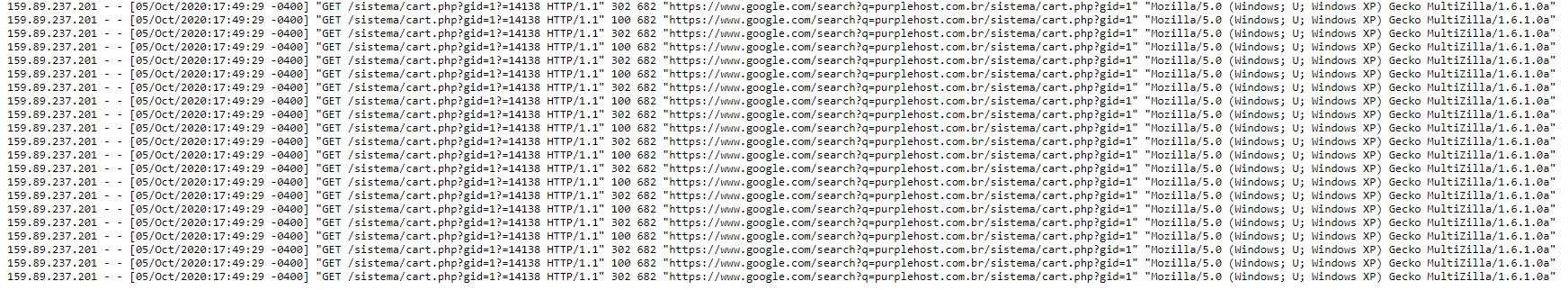
https://purplehost.com.br - Reliable, secure and affordable game hosting.



Comments
You might have a few options with nginx: https://www.nginx.com/blog/mitigating-ddos-attacks-with-nginx-and-nginx-plus/
limit_req_zone and/or limit_conn_zone for location /sistema/ { } should help.
AMD EPYC powered Performance NVMe VPS - Los Angeles, Dallas, New York, Amsterdam, Singapore | Support | Status
I use cPanel shared hosting, unfortunately I can't make this change.
I put the site on the cloudflare network, but it seems that the captcha cannot stop the bots.
https://purplehost.com.br - Reliable, secure and affordable game hosting.
have you tried enabling constant captcha challenge with a firewall rule instead using javascript challenge from under attack mode?
Yes, I am using the challenge (captcha) and yet thousands of requests go through the CF network.
https://purplehost.com.br - Reliable, secure and affordable game hosting.
Well, your domain doesn't seem to go through CF's network and exposes your IP (185.62..). It's not enough to just point your nameservers to CF. You have to click the cloud icon and make it orange (set it to route through CF's networks) and change your origin IP as your old IP is already exposed
I already removed my website from the cloudflare, I would not be a layman to a certain extent of not activating the orange cloud.
https://purplehost.com.br - Reliable, secure and affordable game hosting.
Move your site to BuyVM VPS with ddos protection.
Serious question my friend,
On a shared hosting server, how else do you plan to filter layer 7 attacks?
Nexus Bytes Ryzen Powered NVMe VPS | NYC|Miami|LA|London|Netherlands| Singapore|Tokyo
Storage VPS | LiteSpeed Powered Web Hosting + SSH access | Switcher Special |
how about blocking the referrer? since they use the same referrer on both of your screenshots
Layer 7 attacks do not directly affect the network, but the application, layer 3/4 protection does not protect layer 7.
https://purplehost.com.br - Reliable, secure and affordable game hosting.
How to do this?
https://purplehost.com.br - Reliable, secure and affordable game hosting.
BuyVM filtered-IP is very good at Layer 7 protection.
Since CloudFlare can't mitigate HTTPS I doubt CloudFlare transit can.
ExtraVM
My website is setup with two nginx sites. The frontend site is a reverse proxy to the backend site and has 1-hour cache; the backend site listens on localhost and runs php-fpm.
If someone repeatedly request a page, these requests are answered by the cache and not PHP.
If it's not handled by default we offer all customers custom Layer 7 mitigation rules. I'm happy to help write the rule when I have time if you are not able. It looks like it would be a very simple rule on any number of attributes.
https://www.x4b.net/kb/Layer7Rules
X4B - DDoS Protection: Affordable Anycast DDoS protection including Layer 7 mitigation with PoPs in the Europe, Asia, North and South America.
Latest Offer: Brazil Launch 2020 Offer